Главное меню
Вы здесь
Juniper. Подключение двух SRX туннелями IPsec
чт, 07/06/2018 - 21:07 — vs
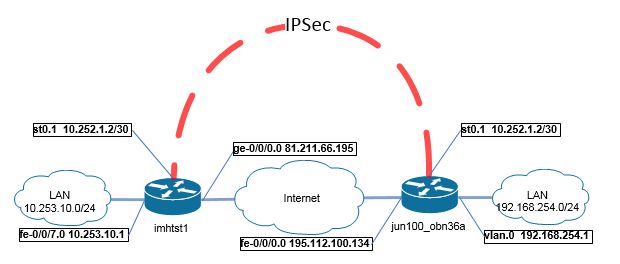
- Создаём Secure Tunnel interface st0.1, и назначаем ему адрес.
jun100_obn36a#set interfaces st0 unit 1 family inet address 10.252.1.2/30 set security zones security-zone vpn interfaces st0.1
imhtst1#
set interfaces st0 unit 1 family inet address 10.252.1.1/30 set security zones security-zone vpn interfaces st0.1
На этом этапе каждый с каждого роутера мы сможем пинговать его туннельный интерфейс.
- Создаём зоны и помещаем туда соответствующие интерфейсы
imhtst1#set security zones security-zone trust address-book address net-imhtst1-10_253_10_0-24 10.253.10.0/24 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/7.0
set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ssh set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust interfaces ge-0/0/0.0
set security zones security-zone vpn address-book address net-obn-192_168_254_0-24 192.168.254.0/24 set security zones security-zone vpn address-book address net-ptp-10_252_1_0-24 10.252.1.0/24 set security zones security-zone vpn host-inbound-traffic system-services all set security zones security-zone vpn host-inbound-traffic protocols all set security zones security-zone vpn interfaces st0.1
jun100_obn36a#
set security zones security-zone trust address-book address net-obn-192_168_254_0-24 192.168.254.0/24 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces vlan.0
set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces fe-0/0/0.0 host-inbound-traffic system-services ping set security zones security-zone untrust interfaces fe-0/0/0.0 host-inbound-traffic system-services ssh set security zones security-zone untrust interfaces fe-0/0/0.0 host-inbound-traffic system-services ike
set security zones security-zone vpn address-book address net-all-10_0_0_0-8 10.0.0.0/8 set security zones security-zone vpn address-book address net-all-172_16_0_0-12 172.16.0.0/12 set security zones security-zone vpn address-book address net-all-192_168_0_0-16 192.168.0.0/16 set security zones security-zone vpn host-inbound-traffic system-services all set security zones security-zone vpn host-inbound-traffic protocols all set security zones security-zone vpn interfaces st0.1
- Создаём политики
imhtst1#set security policies from-zone trust to-zone trust policy trust-to-trust match source-address any set security policies from-zone trust to-zone trust policy trust-to-trust match destination-address any set security policies from-zone trust to-zone trust policy trust-to-trust match application any set security policies from-zone trust to-zone trust policy trust-to-trust then permit
set security policies from-zone trust to-zone untrust policy trust-to-untrust match source-address any set security policies from-zone trust to-zone untrust policy trust-to-untrust match destination-address any set security policies from-zone trust to-zone untrust policy trust-to-untrust match application any set security policies from-zone trust to-zone untrust policy trust-to-untrust then permit
set security policies from-zone trust to-zone vpn policy trust-vpn match source-address net-imhtst1-10_253_10_0-24 set security policies from-zone trust to-zone vpn policy trust-vpn match destination-address net-obn-192_168_254_0-24 set security policies from-zone trust to-zone vpn policy trust-vpn match destination-address net-ptp-10_252_1_0-24 set security policies from-zone trust to-zone vpn policy trust-vpn match application any set security policies from-zone trust to-zone vpn policy trust-vpn then permit set security policies from-zone trust to-zone vpn policy trust-vpn then log session-init set security policies from-zone trust to-zone vpn policy trust-vpn then log session-close set security policies from-zone trust to-zone vpn policy trust-vpn then count
set security policies from-zone vpn to-zone trust policy vpn-trust match source-address net-obn-192_168_254_0-24 set security policies from-zone vpn to-zone trust policy vpn-trust match source-address net-ptp-10_252_1_0-24 set security policies from-zone vpn to-zone trust policy vpn-trust match destination-address net-imhtst1-10_253_10_0-24 set security policies from-zone vpn to-zone trust policy vpn-trust match application any set security policies from-zone vpn to-zone trust policy vpn-trust then permit set security policies from-zone vpn to-zone trust policy vpn-trust then log session-init set security policies from-zone vpn to-zone trust policy vpn-trust then log session-close set security policies from-zone vpn to-zone trust policy vpn-trust then count
set security policies from-zone vpn to-zone vpn policy vpn-to-vpn match source-address any set security policies from-zone vpn to-zone vpn policy vpn-to-vpn match destination-address any set security policies from-zone vpn to-zone vpn policy vpn-to-vpn match application any set security policies from-zone vpn to-zone vpn policy vpn-to-vpn match source-identity any set security policies from-zone vpn to-zone vpn policy vpn-to-vpn then permit set security policies from-zone vpn to-zone vpn policy vpn-to-vpn then log session-init set security policies from-zone vpn to-zone vpn policy vpn-to-vpn then log session-close set security policies from-zone vpn to-zone vpn policy vpn-to-vpn then count
jun100_obn36a#
set security policies from-zone trust to-zone trust policy trust-to-trust match source-address any set security policies from-zone trust to-zone trust policy trust-to-trust match destination-address any set security policies from-zone trust to-zone trust policy trust-to-trust match application any set security policies from-zone trust to-zone trust policy trust-to-trust then permit set security policies from-zone trust to-zone trust policy trust-to-trust then log session-init set security policies from-zone trust to-zone trust policy trust-to-trust then log session-close set security policies from-zone trust to-zone trust policy trust-to-trust then count
set security policies from-zone trust to-zone untrust policy trust-to-untrust match source-address any set security policies from-zone trust to-zone untrust policy trust-to-untrust match destination-address any set security policies from-zone trust to-zone untrust policy trust-to-untrust match application any set security policies from-zone trust to-zone untrust policy trust-to-untrust then permit
set security policies from-zone trust to-zone vpn policy trust-vpn-kma match source-address net-obn-192_168_254_0-24 set security policies from-zone trust to-zone vpn policy trust-vpn-kma match destination-address net-all-10_0_0_0-8 set security policies from-zone trust to-zone vpn policy trust-vpn-kma match destination-address net-all-172_16_0_0-12 set security policies from-zone trust to-zone vpn policy trust-vpn-kma match destination-address net-all-192_168_0_0-16 set security policies from-zone trust to-zone vpn policy trust-vpn-kma match application any set security policies from-zone trust to-zone vpn policy trust-vpn-kma then permit
set security policies from-zone vpn to-zone trust policy vpn-trust-kma match source-address net-all-10_0_0_0-8 set security policies from-zone vpn to-zone trust policy vpn-trust-kma match source-address net-all-172_16_0_0-12 set security policies from-zone vpn to-zone trust policy vpn-trust-kma match source-address net-all-192_168_0_0-16 set security policies from-zone vpn to-zone trust policy vpn-trust-kma match destination-address net-obn-192_168_254_0-24 set security policies from-zone vpn to-zone trust policy vpn-trust-kma match application any set security policies from-zone vpn to-zone trust policy vpn-trust-kma then permit
set security policies from-zone vpn to-zone vpn policy vpn-to-vpn match source-address any set security policies from-zone vpn to-zone vpn policy vpn-to-vpn match destination-address any set security policies from-zone vpn to-zone vpn policy vpn-to-vpn match application any set security policies from-zone vpn to-zone vpn policy vpn-to-vpn match source-identity any set security policies from-zone vpn to-zone vpn policy vpn-to-vpn then permit set security policies from-zone vpn to-zone vpn policy vpn-to-vpn then count
- Создаём ike policy
imhtst1#set security ike policy ike-policy-jun100 mode aggressive set security ike policy ike-policy-jun100 proposal-set compatible set security ike policy ike-policy-jun100 pre-shared-key ascii-text "secretkey"
jun100_obn36a#
set security ike policy ike-policy-imhtst1 mode aggressive set security ike policy ike-policy-imhtst1 proposal-set compatible set security ike policy ike-policy-imhtst1 pre-shared-key ascii-text "secretkey"
- Создаём IKE gateway
imhtst1#set security ike gateway ike-gate-jun100 ike-policy ike-policy-jun100 set security ike gateway ike-gate-jun100 address 195.112.100.134 set security ike gateway ike-gate-jun100 external-interface ge-0/0/0.0
jun100_obn36a#
set security ike gateway ike-gate-imhtst1 ike-policy ike-policy-imhtst1 set security ike gateway ike-gate-imhtst1 address 81.211.66.195 set security ike gateway ike-gate-imhtst1 external-interface fe-0/0/0.0
- Создаём IPSec policy
imhtst1#set security ipsec policy ipsec-policy-jun100 proposal-set compatible
jun100_obn36a#
set security ipsec policy ipsec-policy-imhtst1 proposal-set compatible
- Создаём IPsec VPN, с использованием IKE gateway, IPsec policy
imhtst1#set security ipsec vpn ipsec-vpn-imhtst1 ike gateway ike-gate-jun100 set security ipsec vpn ipsec-vpn-imhtst1 ike ipsec-policy ipsec-policy-jun100 set security ipsec vpn ipsec-vpn-imhtst1 bind-interface st0.1 set security ipsec vpn ipsec-vpn-imhtst1 establish-tunnels immediately
jun100_obn36a#
set security ipsec vpn ipsec-vpn-imh ike gateway ike-gate-imhtst1 set security ipsec vpn ipsec-vpn-imh ike ipsec-policy ipsec-policy-imhtst1 set security ipsec vpn ipsec-vpn-imh bind-interface st0.1 set security ipsec vpn ipsec-vpn-imh establish-tunnels immediately









Добавить комментарий