Главное меню
Вы здесь
Zone Based Firewall (ZBF) troubleshooting
Настройка логирования
Для того, чтобы логи ZBF валились в буфер, настроим logging:
! Настройка отображения текущего времени service timestamps log datetime localtime ! ! Включение логирования logging on ! ! ! Логи на консоль logging console critical logging monitor debugging ! ! Настройка логирования в буфер logging buffered informational logging buffered 16386 logging rate-limit 100 except 4 !
Определяем какие зоны существуют
#show zone security zone self Description: System Defined Zone zone OUTSIDE Member Interfaces: FastEthernet0/0/0 zone INSIDE Member Interfaces: Loopback0 Loopback1 GigabitEthernet0/0 zone TUNNEL Member Interfaces: Tunnel350 Tunnel200
Определение пары зон
Определяем пару зон по направлению
Если нас интересует конкретное направление, например из интерфейса в зоне INSIDE в интерфейс в зоне TUNNEL:
ige01gtw01#show zone-pair security source INSIDE destination TUNNEL Zone-pair name INSIDE-TUNNEL Source-Zone INSIDE Destination-Zone TUNNEL service-policy pm_inside_tunnel
Общий список пар зон
#show zone-pair security Zone-pair name INSIDE-OUTSIDE Source-Zone INSIDE Destination-Zone OUTSIDE service-policy pm_inside-outside Zone-pair name OUTSIDE-INSIDE Source-Zone OUTSIDE Destination-Zone INSIDE service-policy pm_outside-inside Zone-pair name OUTSIDE-SELF Source-Zone OUTSIDE Destination-Zone self service-policy pm_outside-self Zone-pair name SELF-OUTSIDE Source-Zone self Destination-Zone OUTSIDE service-policy pm_self-outside Zone-pair name INSIDE-TUNNEL Source-Zone INSIDE Destination-Zone TUNNEL service-policy pm_inside_tunnel Zone-pair name TUNNEL-INSIDE Source-Zone TUNNEL Destination-Zone INSIDE service-policy pm_tunnel_inside
Отсюда можно отобразить нужные нам service-policy, например посмотрим service-policy pm_inside_tunnel:
ige01gtw01#show policy-map type inspect pm_inside_tunnel Policy Map type inspect pm_inside_tunnel Class cm_temp_drop Drop Class cm_temp_pass_all Pass Class cm_vpn_protocols Pass Class cm_service_protocols Inspect Class cm_sfb-traffic Inspect Class cm_voice_control_traffic Inspect Class cm_inside_tunnel_central_servers Inspect Class cm_inside_tunnel_voice_subnet Inspect Class cm_inside_tunnel_internal_servers Inspect Class cm_inside_tunnel_voice_servers Inspect Class class-default Drop log
или
ige01gtw01#show running-config | section pm_inside_tunnel
policy-map type inspect pm_inside_tunnel class type inspect cm_temp_drop drop class type inspect cm_temp_pass_all pass class type inspect cm_vpn_protocols pass class type inspect cm_service_protocols inspect class type inspect cm_sfb-traffic inspect class type inspect cm_voice_control_traffic inspect class type inspect cm_inside_tunnel_central_servers inspect class type inspect cm_inside_tunnel_voice_subnet inspect class type inspect cm_inside_tunnel_internal_servers inspect class type inspect cm_inside_tunnel_voice_servers inspect class class-default drop
Отдельные Class map можно просмотреть командой:
ige01gtw01#show class-map type inspect cm_voice_control_traffic Class Map type inspect match-any cm_voice_control_traffic (id 8) Match protocol sip Match protocol skinny Match protocol h323
Общая проверка статистики сессий
Данная проверка позволит понять статистику по каждому Class-map. Были ли вообще матчи и сколько прошло пакетов.
Вываливаем всё:
show policy-map type inspect zone-pair
Либо отображаем на уровне пар зон:
show policy-map type inspect zone-pair INSIDE-TUNNEL
Если все нормально, общая статистика должна отображать следующие параметры: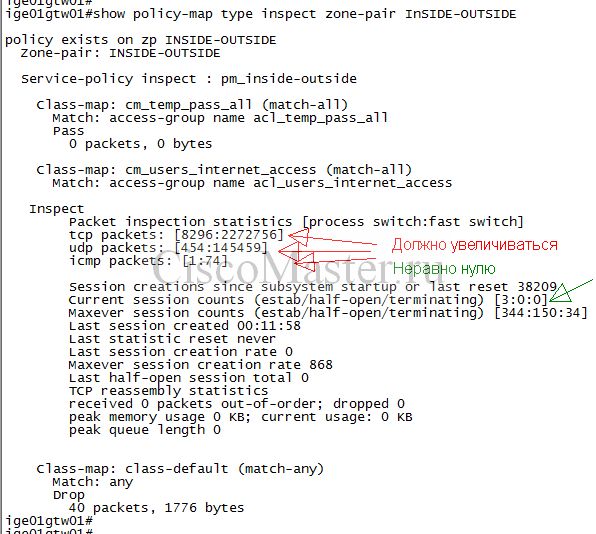
Общая проверка наличия сессий
Здесь можно понять общее количество сессий в данный момент.
show policy-firewall session
Сессии на пару зон:
show policy-firewall session zone-pair INSIDE-OUTSIDE
или более подробная инфа:
show policy-map type inspect zone-pair sessions
Проверка наличия сессий на паре зон
Давайте посмотрим на примере выхода в интернет. Для того чтобы выйти в интернет, должны быть созданы две вещи:
- ip nat translation
- ZBF session
10_5_55_1#show policy-firewall session zone-pair OUTSIDE-SELF | section 37.193.64.214 Session 21B1080 (195.20.104.27:23936)=>(37.193.64.214:22) tcp SIS_OPEN/TCP_ESTAB Created 00:25:37, Last heard 00:00:00 Bytes sent (initiator:responder) [22646:84087] 10_5_55_1#
Поэтому если пинг удачен, мы увидим следующее:
#show policy-map type inspect zone-pair INSIDE-OUTSIDE sessions | section 192.168.48.13 Session 155390E0 (192.168.48.13:8)=>(8.8.8.8:0) icmp SIS_OPEN Created 00:00:09, Last heard 00:00:05 ECHO request Bytes sent (initiator:responder) [128:128]
#show ip nat translations | include 192.168.48.13 icmp 193.105.126.147:1 192.168.48.13:1 8.8.8.8:1 8.8.8.8:1
Исследуем конкретную сессию по IP:
show policy-firewall session zone-pair INSIDE-TUNNEL | section 10.5.55.254

Проверка сессий в каждой policy-map
Предположим, что у нас следующая service-policy:
policy-map type inspect pm_inside_tunnel class type inspect cm_temp_drop drop class type inspect cm_temp_pass_all pass class type inspect cm_vpn_protocols pass class type inspect cm_service_protocols inspect class type inspect cm_sfb-traffic inspect class type inspect cm_voice_control_traffic inspect class type inspect cm_inside_tunnel_central_servers inspect class type inspect cm_inside_tunnel_voice_subnet inspect class type inspect cm_inside_tunnel_internal_servers inspect class type inspect cm_inside_tunnel_voice_servers inspect class class-default drop log
Мы можем посмотреть сессии, а также принадлежность созданных сессий к Policy-map:
ige01gtw01#show policy-map type inspect zone-pair policy exists on zp INSIDE-OUTSIDE Zone-pair: INSIDE-OUTSIDE Service-policy inspect : pm_inside-outside Class-map: cm_temp_pass_all (match-all) Match: access-group name acl_temp_pass_all Pass 0 packets, 0 bytes Class-map: cm_users_internet_access (match-all) Match: access-group name acl_users_internet_access Inspect Packet inspection statistics [process switch:fast switch] tcp packets: [8327:2280522] udp packets: [454:145475] icmp packets: [1:126] Session creations since subsystem startup or last reset 38294 Current session counts (estab/half-open/terminating) [4:0:0] Maxever session counts (estab/half-open/terminating) [344:150:34] Last session created 00:08:53 Last statistic reset never Last session creation rate 0 Maxever session creation rate 868 Last half-open session total 0 TCP reassembly statistics received 0 packets out-of-order; dropped 0 peak memory usage 0 KB; current usage: 0 KB peak queue length 0 Class-map: class-default (match-any) Match: any Drop 40 packets, 1776 bytes policy exists on zp OUTSIDE-INSIDE Zone-pair: OUTSIDE-INSIDE Service-policy inspect : pm_outside-inside Class-map: cm_temp_pass_all (match-all) Match: access-group name acl_temp_pass_all Pass 0 packets, 0 bytes Class-map: cm_server1_services (match-all) Match: access-group name acl_server1_ip Match: class-map match-any cm_server1_protocols Match: protocol smtp 0 packets, 0 bytes 30 second rate 0 bps Inspect Session creations since subsystem startup or last reset 0 Current session counts (estab/half-open/terminating) [0:0:0] Maxever session counts (estab/half-open/terminating) [0:0:0] Last session created never Last statistic reset never Last session creation rate 0 Maxever session creation rate 0 Last half-open session total 0 TCP reassembly statistics received 0 packets out-of-order; dropped 0 peak memory usage 0 KB; current usage: 0 KB peak queue length 0 ige01gtw01#show policy-map type inspect zone-pair INSIDE-TUNNEL sessions policy exists on zp INSIDE-TUNNEL Zone-pair: INSIDE-TUNNEL Service-policy inspect : pm_inside_tunnel Class-map: cm_temp_drop (match-all) Match: access-group name acl_temp_drop Drop 0 packets, 0 bytes Class-map: cm_temp_pass_all (match-all) Match: access-group name acl_temp_pass_all Pass 0 packets, 0 bytes Class-map: cm_vpn_protocols (match-all) Match: access-group name acl_vpn_protocols Pass 0 packets, 0 bytes Class-map: cm_service_protocols (match-any) Match: protocol tacacs 0 packets, 0 bytes 30 second rate 0 bps Match: protocol radius 0 packets, 0 bytes 30 second rate 0 bps Match: protocol icmp 956 packets, 18897 bytes 30 second rate 0 bps Match: protocol ntp 4706 packets, 269576 bytes 30 second rate 0 bps Inspect Class-map: cm_sfb-traffic (match-all) Match: access-group name acl_user-sfb-traffic Inspect Class-map: cm_voice_control_traffic (match-any) Match: protocol sip 0 packets, 0 bytes 30 second rate 0 bps Match: protocol skinny 164 packets, 6336 bytes 30 second rate 0 bps Match: protocol h323 0 packets, 0 bytes 30 second rate 0 bps Inspect Number of Established Sessions = 10 Established Sessions Session 155439E0 (192.168.49.11:35078)=>(10.19.65.11:2000) skinny:tcp SIS_OPEN/TCP_ESTAB Created 04:10:51, Last heard 00:00:06 Bytes sent (initiator:responder) [8345:10236] Session 1554A660 (192.168.49.13:35689)=>(10.19.65.11:2000) skinny:tcp SIS_OPEN/TCP_ESTAB Created 04:10:49, Last heard 00:00:15 Bytes sent (initiator:responder) [8073:9164] Session 1554C5E0 (192.168.49.4:35213)=>(10.19.65.11:2000) skinny:tcp SIS_OPEN/TCP_ESTAB Created 04:10:48, Last heard 00:00:14 Bytes sent (initiator:responder) [8072:9168] Session 15540FE0 (192.168.49.5:35273)=>(10.19.65.11:2000) skinny:tcp SIS_OPEN/TCP_ESTAB Created 04:08:52, Last heard 00:00:12 Bytes sent (initiator:responder) [8024:9116] Session 15543D60 (192.168.49.13:35696)=>(10.19.65.12:2000) skinny:tcp SIS_OPEN/TCP_ESTAB Created 04:08:48, Last heard 00:00:45 Bytes sent (initiator:responder) [2976:0] Session 155408E0 (192.168.49.4:35220)=>(10.19.65.12:2000) skinny:tcp SIS_OPEN/TCP_ESTAB Created 04:08:48, Last heard 00:00:44 Bytes sent (initiator:responder) [2976:0] Session 1554C260 (192.168.49.5:35274)=>(10.19.65.12:2000) skinny:tcp SIS_OPEN/TCP_ESTAB Created 04:08:44, Last heard 00:00:44 Bytes sent (initiator:responder) [2976:0] Session 15545960 (192.168.49.11:35085)=>(10.19.65.12:2000) skinny:tcp SIS_OPEN/TCP_ESTAB Created 04:08:50, Last heard 00:00:44 Bytes sent (initiator:responder) [2976:0] Session 2EB2700 (192.168.49.10:35153)=>(10.19.65.11:2000) skinny:tcp SIS_OPEN/TCP_ESTAB Created 04:06:18, Last heard 00:00:03 Bytes sent (initiator:responder) [8222:10112] Session 1552EC60 (192.168.49.10:35154)=>(10.19.65.12:2000) skinny:tcp SIS_OPEN/TCP_ESTAB Created 04:06:17, Last heard 00:00:17 Bytes sent (initiator:responder) [2952:0]
Например посмотрим все подключения снаружи:
10_5_26_1#show policy-map type inspect zone-pair OUTSIDE-SELF sessions policy exists on zp OUTSIDE-SELF Zone-pair: OUTSIDE-SELF Service-policy inspect : pm_outside-self Class-map: cm_temp_pass_all (match-all) Match: access-group name acl_temp_pass_all Pass 0 packets, 0 bytes Class-map: cm_vpn_protocols (match-all) Match: access-group name acl_vpn_protocols Pass 554379 packets, 299230930 bytes Class-map: cm_outside_self_ssh (match-all) Match: access-group 23 Match: access-group name acl_ssh Inspect Number of Established Sessions = 1 Established Sessions Session 11F63B00 (46.28.95.136:54887)=>(217.13.221.187:22) tcp SIS_OPEN/TCP_ESTAB Created 03:34:11, Last heard 00:00:00 Bytes sent (initiator:responder) [142359:605659] Class-map: cm_outside_self_icmp (match-all) Match: protocol icmp Inspect Number of Established Sessions = 1 Established Sessions Session 2722160 (46.28.95.136:8)=>(217.13.221.187:0) icmp SIS_OPEN Created 00:00:10, Last heard 00:00:00 ECHO request Bytes sent (initiator:responder) [352:352] Class-map: class-default (match-any) Match: any Drop 848 packets, 30030 bytes
Мы видим подключение по SSH и наличие пингов.
Здесь можно вытащить информацию кто пингует, когда был последний пинг, и насколько давно уже пингуют.
Предположим у нас не открываются папки от 192.168.48.13 на хост 192.168.2.12 - выясним причину
Для выяснения причины сначала включим лог на нужной нам service-policy:
(config)#policy-map type inspect pm_inside_tunnel (config-pmap)#class class-default (config-pmap-c)#drop log
При повторении попытки мы увидим сообщение в логе:
Dec 14 13:29:17.579: %FW-6-DROP_PKT: Dropping tcp session 192.168.48.13:49286 192.168.2.12:445 on zone-pair INSIDE-TUNNEL class class-default due to DROP action found in policy-map with ip ident 22893
Удаление всех сессий
ZBF:
clear zone-pair TUNNEL-INSIDE inspect session
NAT:
clear ip nat translation *









Добавить комментарий