Главное меню
Вы здесь
Cisco ASA 8.4.2 с нуля. Часть 11. Threat Detection
Threat Detection позволяет "мониторить вторжения" и информирует Администратора о возможных атаках.
Threat Detection не является заменой IDS/IPS, и используется в случае недоступности функций IDS/IPS.
Существуют следующие компоненты Threat Detection:
- Basic Threat Detection
- Advanced Threat Detection
- Scanning Threat Detection
Basic Threat Detection
Basic Threat Detection имеет чисто информационный характер, и не выполняет каких-то действий для предотвращения атак.
Basic Threat Detection заключается в общем мониторинге dropped packets для следующих events:
Packes denied by Access Lists (ACL Drop).
Bad packet format (such as invalid-ip-header or invalid-tcp-hdr-length).
Connection limits exceeded (both system-wide resource limits, and limits set in theconfiguration).
DoS attack detected (such as an invalid SPI, Stateful Firewall check failure).
Basic firewall checks failed (This option is a combined rate that includes all firewallrelated packet drops in this bulleted list. It does not include non-firewall-related drops such as interface overload, packets failed at application inspection, and scanning attack detected.)
Suspicious ICMP packets detected.
Packets failed application inspection.
Interface overload.
Scanning attack detected (This option monitors scanning attacks; for example, the first TCP packet is not a SYN packet, or the TCP connection failed the 3-way handshake. Full scanning threat detection takes this scanning attack rate information and acts on it by classifying hosts as attackers and automatically shunning them, for example.)
SYN Attack Detection. Incomplete session detection such as TCP SYN attack detected or no data UDP session attack detected.
Как работает Threat Detection.
Average Rate Interval (ARI) - это интервал времени, в котором измеряются количество Packet Drop.
Если в интервале ARI количество Packet Drop превышает заданный уровень threshold, ASA считает что произошел threat, - и генерит в лог system log message (733100).
Basic threat detection включает два threshold, которые можно настраивать:
- average rate - это среднее число drops per second, посчитанное для заданного ARI.
- burst rate -
Настройка Basic Threat Detection
Basic Threat Detection включена по умолчанию.
Вручную включить можно командой:
threat-detection basic-threat
Либо через ASDM: Configuration>Firewall>Threat Detection
Просмотр статистики:
show threat-detection rate Average(eps) Current(eps) Trigger Total events 10-min ACL drop: 2 0 0 1334 1-hour ACL drop: 0 2 0 2017 10-min SYN attck: 0 0 0 267 1-hour SYN attck: 0 0 0 699 10-min Scanning: 3 1 4 1926 1-hour Scanning: 1 3 0 3726 10-min Bad pkts: 0 0 0 18 1-hour Bad pkts: 0 0 0 65 10-min Firewall: 2 1 0 1659 1-hour Firewall: 0 2 0 3027 10-min DoS attck: 0 0 0 307 1-hour DoS attck: 0 0 0 945 10-min Interface: 2 0 0 1720 1-hour Interface: 1 1 0 3671
Здесь нас больше всего интересует столбец Trigger: в данном примере было обнаружено 4 атаки типа Scanning.
Посмотреть установки Basic Threat Detection events:
show running-config all threat-detection
Установки можно поменять.
Advanced Threat Detection
Advanced threat detection - это также лишь статистика, но более подробная.
Advanced Threat Detection позволяет определить traffic rates для hosts, ports, protocols, ACLs.
Advanced threat detection может перегрузить ресурсы системы!!!
Включение:
- threat-detection statistics port number-of-rate 1 - статистика по TCP/UDP портам
- threat-detection statistics protocol number-of-rate 1 - cтатистика по протоколам IP, non-TCP/UDP.
- threat-detection statistics host number-of-rate 1 - статистика по хостам.
- threat-detection statistics access-list - статистика по ACL
- threat-detection statistics tcp-intercept
- hpm topN enable
Здесь number-of-rate означает количество отслеживаемых rate intervals. Доступно 1-3 и чем больше, тем больше необходимо ресурсов.
1-отслеживается за 1 hour.
2-отслеживается за 1 hour, 8 hours.
3-отслеживается за 1 hour, 8 hours, and 24 hours.
threat-detection statistics port number-of-rate 1 threat-detection statistics protocol number-of-rate 1 threat-detection statistics host number-of-rate 1 threat-detection statistics access-list threat-detection statistics tcp-intercept hpm topN enable
Scanning Threat Detection
Scanning Threat Detection способна также и блокировать attacker.
Scanning Threat Detection может перегрузить ресурсы системы!!!
Конфигурация:
threat-detection scanning-threat shun threat-detection scanning-threat shun duration 3600 threat-detection scanning-threat shun except ip-address 10.1.1.1 255.255.255.0
Проверка:
show threat-detection shun
show threat-detection scanning-threat
Поведение в реальных ситуациях
В случае подозрения что у нас какие-то проблемы, первое что следует сделать - открыть ASDM, и посмотреть Firewall Dashboard.
Ниже приведён пример реакции ASA на сканирование извне через nmap. Поскольку при сканировании перебираются порты, мы получим массу ACL Dropped и Possble Scans.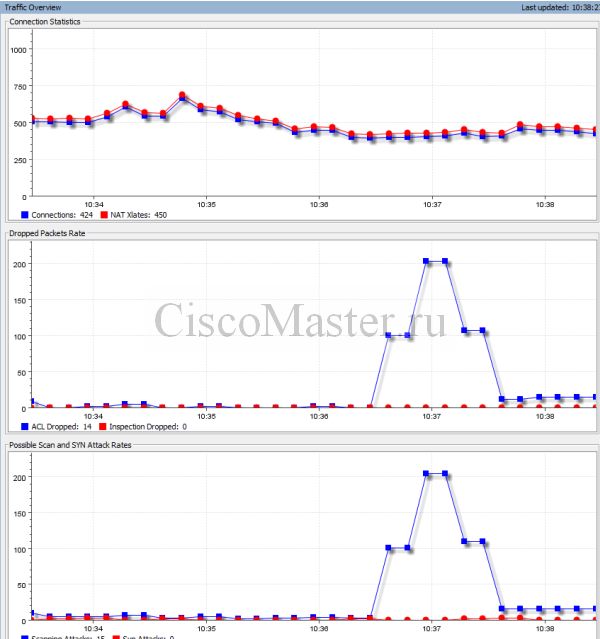
Далее смотрим логи:
May 05 2017 10:41:03: %ASA-4-733100: [ Scanning] drop rate-1 exceeded. Current burst rate is 4 per second, max configured rate is 10; Current average rate is 12 per second, max configured rate is 5; Cumulative total count is 7530
May 05 2017 10:41:03: %ASA-4-733100: [ Scanning] drop rate-2 exceeded. Current burst rate is 0 per second, max configured rate is 8; Current average rate is 5 per second, max configured rate is 4; Cumulative total count is 18327
May 05 2017 10:41:23: %ASA-4-733100: [ Scanning] drop rate-1 exceeded. Current burst rate is 4 per second, max configured rate is 10; Current average rate is 12 per second, max configured rate is 5; Cumulative total count is 7517
Как видно, в логах валятся ругань на threat category [ Scanning].
Соответственно мы увидим что будут расти счётчики Scanning:
show threat-detection rate
msk-asa-01# show threat-detection rate Average(eps) Current(eps) Trigger Total events 10-min ACL drop: 9 8 0 5709 1-hour ACL drop: 4 8 0 17583 10-min SYN attck: 0 0 0 200 1-hour SYN attck: 0 0 0 1458 10-min Scanning: 10 9 599 6164 1-hour Scanning: 5 9 559 20978 10-min Bad pkts: 0 0 0 19 1-hour Bad pkts: 0 0 0 176 10-min Firewall: 9 9 0 5964 1-hour Firewall: 5 8 0 19520 10-min DoS attck: 0 0 0 236 1-hour DoS attck: 0 0 0 1761 10-min Interface: 12 27 0 7684 1-hour Interface: 5 8 0 20677
Трафик массово дропается, посмотрим причины:
show asp drop
msk-asa-01# show asp drop Frame drop: No valid adjacency (no-adjacency) 208 No route to host (no-route) 248 Flow is denied by configured rule (acl-drop) 146493 First TCP packet not SYN (tcp-not-syn) 5668 TCP Dual open denied (tcp-dual-open) 30 TCP data send after FIN (tcp-data-past-fin) 8 TCP failed 3 way handshake (tcp-3whs-failed) 2374 TCP RST/FIN out of order (tcp-rstfin-ooo) 8020 TCP packet SEQ past window (tcp-seq-past-win) 671 TCP Out-of-Order packet buffer full (tcp-buffer-full) 3 TCP Out-of-Order packet buffer timeout (tcp-buffer-timeout) 700 TCP RST/SYN in window (tcp-rst-syn-in-win) 7 TCP dup of packet in Out-of-Order queue (tcp-dup-in-queue) 9 TCP packet failed PAWS test (tcp-paws-fail) 37 Slowpath security checks failed (sp-security-failed) 86550 ICMP Inspect bad icmp code (inspect-icmp-bad-code) 72 ICMP Inspect seq num not matched (inspect-icmp-seq-num-not-matched) 2 FP L2 rule drop (l2_acl) 38192 Interface is down (interface-down) 5 Dropped pending packets in a closed socket (np-socket-closed) 575 Connection to PAT address without pre-existing xlate (nat-no-xlate-to-pat-pool) 29377 Last clearing: Never Flow drop: Inspection failure (inspect-fail) 896 Last clearing: Never
Повторяем эту команду несколько раз и получим, что увеличивается счетчик
Flow is denied by configured rule (acl-drop)
Ну и наконец вычисляем кто именно нас атакует:
capture drop type asp-drop real-time
msk-asa-01# capture drop type asp-drop real-time Warning: using this option with a slow console connection may result in an excessive amount of non-displayed packets due to performance limitations. Use ctrl-c to terminate real-time capture 1: 10:54:16.344876 192.168.2.49.137 > 192.168.2.255.137: udp 50 2: 10:54:16.369655 195.112.100.134.40584 > 46.28.95.136.10778: S 2228624278:2228624278(0) win 10243: 10:54:16.370220 195.112.100.134.40584 > 46.28.95.136.16113: S 2228624278:2228624278(0) win 1024 Drop-reason: (acl-drop) Flow is denied by configured rule 4: 10:54:16.371288 195.112.100.134.40584 > 46.28.95.136.7025: S 2228624278:2228624278(0) win 1024 5: 10:54:16.371410 195.112.100.134.40584 > 46.28.95.136.6779: S 2228624278:2228624278(0) win 1024 Drop-reason: (acl-drop) Flow is denied by configured rule 6: 10:54:16.372310 195.112.100.134.40584 > 46.28.95.136.1198: S 2228624278:2228624278(0) win 1024 Drop-reason: (acl-drop) Flow is denied by configured rule 7: 10:54:16.373271 195.112.100.134.40584 > 46.28.95.136.31337: S 2228624278:2228624278(0) win 1024 Drop-reason: (acl-drop) Flow is denied by configured rule 8: 10:54:16.373378 195.112.100.134.40584 > 46.28.95.136.2170: S 2228624278:2228624278(0) win 1024 9: 10:54:16.374004 195.112.100.134.40584 > 46.28.95.136.9485: S 2228624278:2228624278(0) win 1024 Drop-reason: (acl-drop) Flow is denied by configured rule 10: 10:54:16.375102 195.112.100.134.40584 > 46.28.95.136.45100: S 2228624278:2228624278(0) win 1024 Drop-reason: (acl-drop) Flow is denied by configured rule
Это будет сразу видно по большому количеству дропов трафика от одного источника, т.е. от 195.112.100.134.
Подробнее см.
ASA Threat Detection Functionality and Сonfiguration
http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-nex...









Добавить комментарий