Главное меню
Вы здесь
Построение ASA VPN Site-to-Site с использованием IKEv2 IPSec
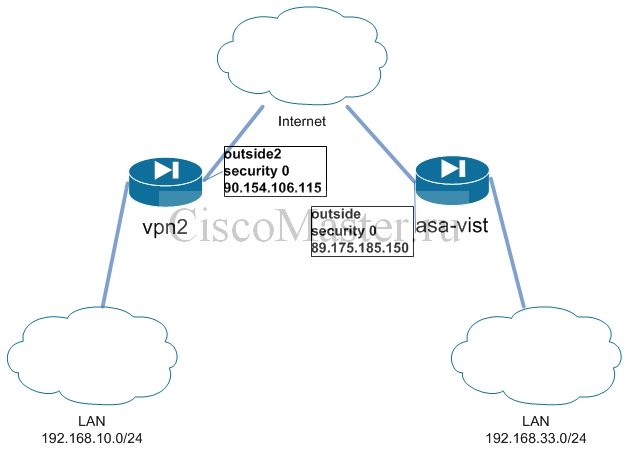
Появилась необходимость построить туннель между двумя ASA версий 9.2(2)4 и не удалось завести IKEv1 IPSec.
Заработал только IKEv2 IPSec со следующей конфигурацией:
Step1: Configure Interesting Traffic to be encrypted
asa-vist
access-list 33_to_center_acl extended permit ip 192.168.33.0 255.255.255.0 192.168.10.0 255.255.255.0
vpn2
access-list center_to_33_acl extended permit ip 192.168.10.0 255.255.255.0 192.168.33.0 255.255.255.0
NAT Exclusion for VPN Traffic
asa-vist
object-group network obj-local network-object 192.168.33.0 255.255.255.0 ! object-group network obj-remote network-object 192.168.10.0 255.255.255.0 ! nat (inside,outside) source static obj-local obj-local destination static obj-remote obj-remote no-proxy-arp route-lookup
vpn2
NAT Exclusion for VPN Traffic object-group network obj-local network-object 192.168.10.0 255.255.255.0 ! object-group network obj-remote network-object 192.168.33.0 255.255.255.0 ! nat (inside,outside2) source static obj-local obj-local destination static obj-remote obj-remote no-proxy-arp route-lookup
###
Step2: Configure IKEv2 Policy (similar to Phase1 in IKEv1)
asa-vist
crypto ikev2 policy 1 encryption des integrity sha group 2 prf sha lifetime seconds 43200
vpn2
crypto ikev2 policy 1 encryption des integrity sha group 2 prf sha lifetime seconds 43200
###
Step3: Configure IKEv2 IPSEC Proposal (similar to transform-set in IKEv1)
asa-vist
crypto ipsec ikev2 ipsec-proposal DES protocol esp encryption des protocol esp integrity sha-1 md5
vpn2
crypto ipsec ikev2 ipsec-proposal DES protocol esp encryption des protocol esp integrity sha-1 md5
###
Step4: Configure IKEv1 Policies and Transform Sets
asa-vist
crypto ikev1 policy 10 authentication pre-share encryption des hash sha group 2 lifetime 86400 ! crypto isakmp identity address ! crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
vpn2
crypto ikev1 policy 10 authentication pre-share encryption des hash sha group 2 lifetime 86400 ! crypto isakmp identity address ! crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
###
Step5: Configure a Group Policy to allow both IKEv1 and IKEv2
asa-vist
group-policy GroupPolicy_90.154.106.115 internal group-policy GroupPolicy_90.154.106.115 attributes vpn-tunnel-protocol ikev1 ikev2
vpn2
group-policy GroupPolicy_89.175.185.150 internal group-policy GroupPolicy_89.175.185.150 attributes vpn-tunnel-protocol ikev1 ikev2
###
Step6: Configure Crypto Maps with both IKEv1 and IKEv2 IPSEC Profiles
asa-vist
crypto map outside_map 1 match address 33_to_center_acl crypto map outside_map 1 set peer 90.154.106.115 crypto map outside_map 1 set ikev1 transform-set ESP-DES-SHA crypto map outside_map 1 set ikev2 ipsec-proposal DES crypto map outside_map interface outside
vpn2
crypto map outside_map 1 match address center_to_33_acl crypto map outside_map 1 set peer 89.175.185.150 crypto map outside_map 1 set ikev1 transform-set ESP-DES-SHA crypto map outside_map 1 set ikev2 ipsec-proposal DES crypto map outside_map interface outside2
###
Step7: Configure Crypto Maps with both IKEv1 and IKEv2 IPSEC Profiles
asa-vist
tunnel-group 90.154.106.115 type ipsec-l2l tunnel-group 90.154.106.115 general-attributes default-group-policy GroupPolicy_90.154.106.115 tunnel-group 90.154.106.115 ipsec-attributes ikev1 pre-shared-key cisco123 ikev2 remote-authentication pre-shared-key cisco1234 ikev2 local-authentication pre-shared-key cisco1
vpn2
tunnel-group 89.175.185.150 type ipsec-l2l tunnel-group 89.175.185.150 general-attributes default-group-policy GroupPolicy_89.175.185.150 tunnel-group 89.175.185.150 ipsec-attributes ikev1 pre-shared-key cisco123 ikev2 remote-authentication pre-shared-key cisco1 ikev2 local-authentication pre-shared-key cisco1234
###
Step8: Enable both IKEv1 and IKEv2 on outside interface
asa-vist
crypto ikev2 enable outside crypto ikev1 enable outside
vpn2
crypto ikev2 enable outside crypto ikev1 enable outside
Проверка
От asa-vist:
ping tcp inside 192.168.10.45 80 source 192.168.33.10 1036
show crypto isakmp sa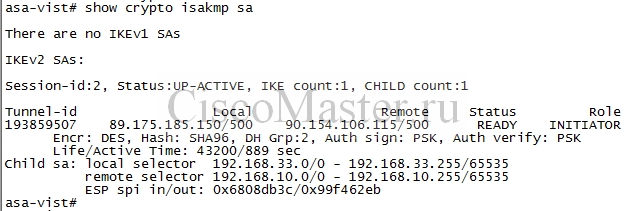
show crypto ipsec sa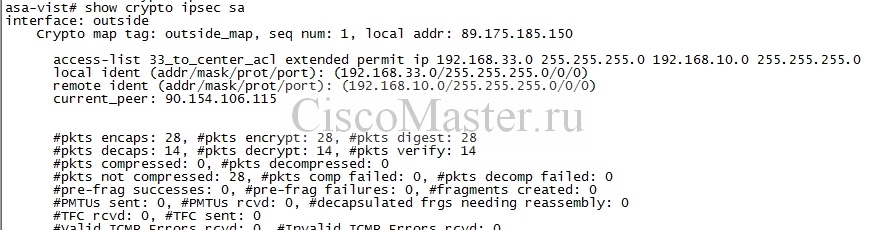









Комментарии
А для какой цели пользовать и
А для какой цели пользовать и разрешать обе версии IKE?
Добавить комментарий